If you’re an IT administrator and want to prevent your clients from turning off BitLocker encryption or decrypting their drives, this article is for you. Note that if the client’s account is a standard account, it can’t turn off BitLocker as the decrypting process requires administrative privileges. So if you change user account type to standard user, you can prevent turning off BiLocker from your clients.
However, if client’s account have admin privileges, they can simply turn off BitLocker and decrypt their drive. To prevent this, you can create an AppLocker rule and deploy it to client’s machine. Here is the how-to part:
How To Prevent Administrators From Turning Off BitLocker In Windows 10/8.1/7
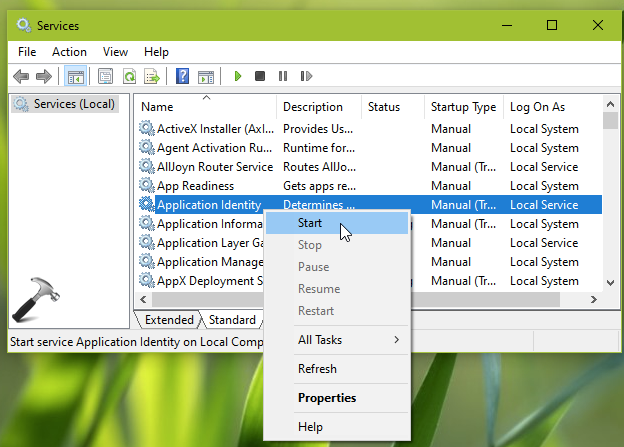
1. Open Services snap-in by running services.msc command.
2. In Services snap-in, make sure Application Identity service is running. You can right click on this service and select Start, if it isn’t running.
3. Then press  + R and put
+ R and put secpol.msc in Run dialog box to open Security Policy snap-in. Click OK.
4. Next, in the Security Policy snap-in window, navigate here:
Security Settings > Application Control Policies > AppLocker > Executable Rules
5. Right click on Executable Rules, select Create New Rule.
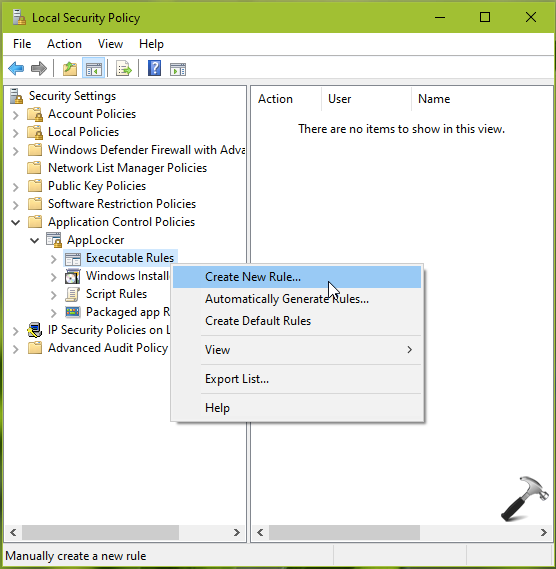
6. Under Create Executable Rules, on Permissions tab, select Action Deny. Then select the administrator accounts or users which you want to prevent turning off BitLocker. Click Next.
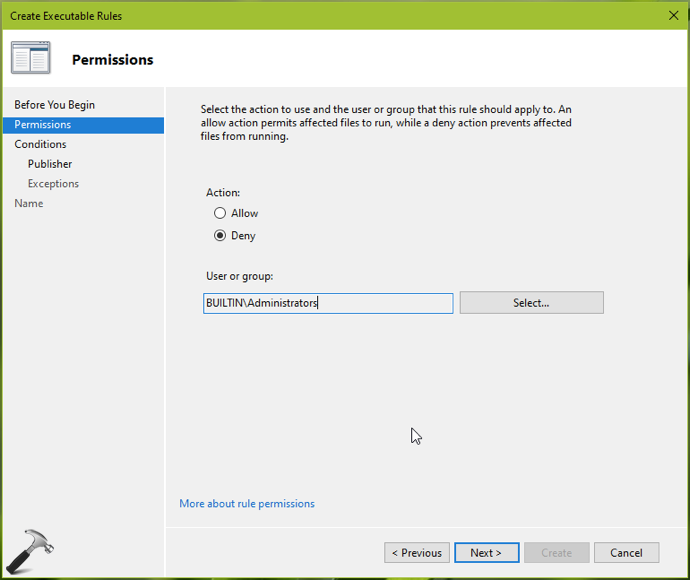
7. On the next section, select Publisher and click Next.

8. Under Publisher, browse to C:\Windows\System32 and select manage-bde.exe file. Click Next.

9. Under Name, provide a justified description and click Create.
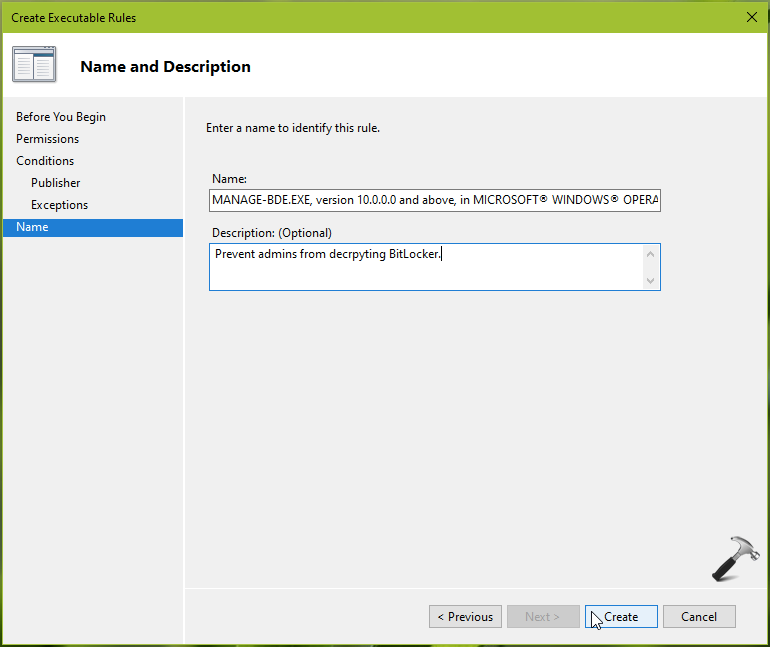
10. Then for AppLocker warning prompt, click Yes.

11. Finally, we’ve created the rule to prevent administrators from turning off BitLocker.

12. Close Security Policy snap-in and run gpupdate /force command to update machine policies on client system.
Now when administrators or users try to turn off BitLocker, they should get Access denied error as the policy is controlled by Group Policy. However, clients can still turn on BitLocker as usual, but can’t turn it off.
Check this video to illustrate above steps:
That’s it!
![KapilArya.com is a Windows troubleshooting & how to tutorials blog from Kapil Arya [Microsoft MVP (Windows IT Pro)]. KapilArya.com](https://images.kapilarya.com/Logo1.svg)







![[Latest Windows 10 Update] What’s new in KB5055612? [Latest Windows 10 Update] What’s new in KB5055612?](https://www.kapilarya.com/assets/Windows10-Update.png)


8 Comments
Add your comment
Hi Kapil, but what about the local admin user disabling the AppLocker Policy?
^^ Tom, if you’re deploying this policy via DC, local admin users may not able to suppress it.
Hi Kapil, I just try you method. Seems it no longer work today. The local admins can still disable the bitlocker even with the policy. Do you have any update on this method? Thanks.
^^ Are you Windows 11 or 10? Have you tried the steps exactly?
Hi Kapil, I am using Windows 10 and I followed all your steps exactly. When I test it with local admin, it doesn’t reject me and just starts to decrypt
^^ Check step 6, make sure you select Deny and added correct group/users.
Hi Kapil, no matter I select the built in Administrators group or the built in user Administrator in step 6, I can decrypt using the built in user Administrator.
How to enable bitlocker command for certain users via GPO?