When we opt to use Remote Desktop, we must ensure the security of our systems. Usually, when remote connections are made, the user should be asked to input their user name and password. By default, Windows will block those users having blank password.
But if same is not occurring on your system, you should try below mentioned methods to block clients with blank password. Microsoft further recommends ‘blank passwords are a serious threat to computer security and they should be forbidden through both corporate policy and suitable technical measures’.
Page Contents
Limit Local Account Use Of Blank Passwords To Console Logon Only
Method 1 – Using Security Policy Editor
1. Press  + R and put
+ R and put secpol.msc in Run dialog box. Click OK to open Security Policy snap-in.
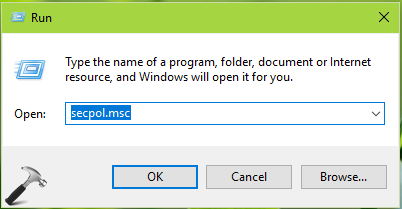
2. Then in Security Policy snap-in window, navigate here:
Security Settings > Local Policies > Security Options
3. In the right pane of Security Options, locate and double click on the Accounts: Limit local account use of blank passwords to console logon only policy setting.
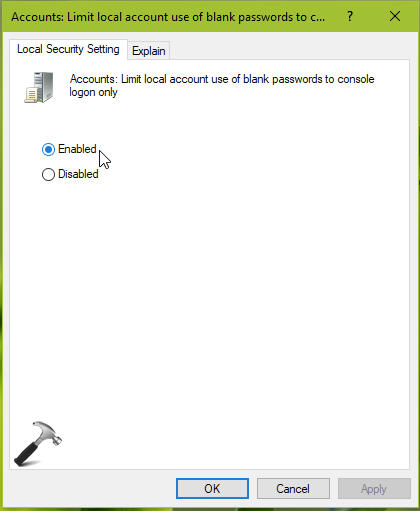
4. Set the policy setting to Enabled and click Apply. Close Security Policy snap-in.
Windows will now start blocking clients with blank password.
Method 2 – Using Registry Editor
1. Open Registry Editor by running regedit command.
2. Go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa.
3. In the right pane of Lsa, double click and set the LimitBlankPasswordUse registry DWORD (REG_DWORD) to 1.

4. Close Registry Editor and reboot to make changes effective.
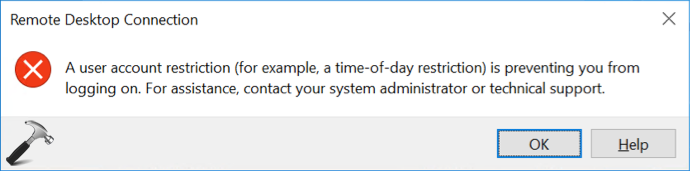
After restarting your system, Windows will apply your configured user account restriction. So now when users with blank password try to connect to RDP, they’ll receive following error:
A user account restriction (for example, a time-of-day restriction) is preventing you from logging on. For assistance, contact your system administrator or technical support.
That’s it!
![KapilArya.com is a Windows troubleshooting & how to tutorials blog from Kapil Arya [Microsoft MVP (Windows IT Pro)]. KapilArya.com](https://images.kapilarya.com/Logo1.svg)






![[Latest Windows 10 Update] What’s new in KB5055612? [Latest Windows 10 Update] What’s new in KB5055612?](https://www.kapilarya.com/assets/Windows10-Update.png)




Leave a Reply