Recently, Microsoft has identified Windows Elevation of Privilege Vulnerability (CVE-2021-36934). It affects users on some Windows operating systems. According to the company, an attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges. The attacker could then install programs, view, change, or delete data or create new accounts with full user rights. Microsoft considers this as an important vulnerability and in this article, we’ll see how to fix it.
Initially, the company has identified this vulnerability for Windows 10 and Server operating systems. The company is currently working on a fix that may be offered via upcoming updates. As of now, you can try the workaround shared by Microsoft, mentioned next in this article. Following Windows operating systems are currently affected with CVE-2021-36934:
- Windows Server, version 20H2 (Server Core Installation)
- Windows 10 Version 20H2 for ARM64-based Systems
- Windows 10 Version 20H2 for 32-bit Systems
- Windows 10 Version 20H2 for x64-based Systems
- Windows Server, version 2004 (Server Core installation)
- Windows 10 Version 2004 for x64-based Systems
- Windows 10 Version 2004 for ARM64-based Systems
- Windows 10 Version 2004 for 32-bit Systems
- Windows 10 Version 21H1 for 32-bit Systems
- Windows 10 Version 21H1 for ARM64-based Systems
- Windows 10 Version 21H1 for x64-based Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows Server 2019 (Server Core installation)
- Windows Server 2019
- Windows 10 Version 1809 for ARM64-based Systems
- Windows 10 Version 1809 for x64-based Systems
- Windows 10 Version 1809 for 32-bit Systems
So if you’re on any of the above mentioned systems, here’s how you can fix it.
How to fix Windows Elevation of Privilege Vulnerability (CVE-2021-36934)
To check, if you’ve really affected with this vulnerability, try following the steps:
1. Open administrative Command Prompt.
2. Then execute following command:
icacls %windir%\system32\config\sam
3. If this command mentions BUILTIN\Users in results, then your system is vulnerable.
Here’s how to fix, if your system is vulnerable:
1. Press  + R to and select Command Prompt (Admin).
+ R to and select Command Prompt (Admin).
2. Then execute this command to restrict access to the contents of %windir%\system32\config:
icacls %windir%\system32\config\*.* /inheritance:e
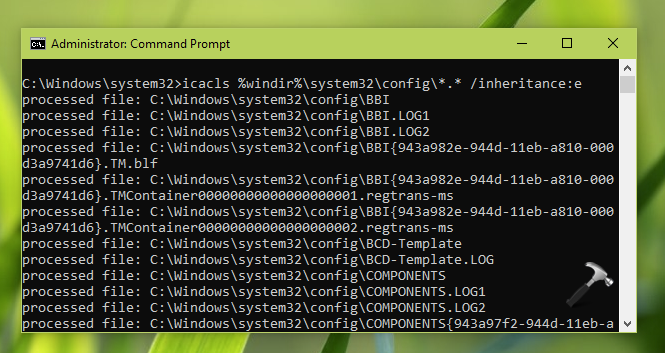
3. Next, execute this command:
vssadmin list shadows /for=%systemdrive%
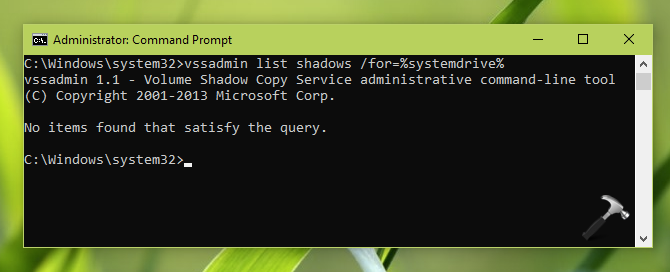
If you see No items found that satisfy the query, this means you’re now safe.
If you don’t see No items found that… message, delete all shadow copies of the system drive with this command:
vssadmin delete shadows /for=%systemdrive% /Quiet
For further information, you can refer this support article.
This article will be updated when Microsoft will release the fix for above issue with Windows Update.
That’s it!
![KapilArya.com is a Windows troubleshooting & how to tutorials blog from Kapil Arya [Microsoft MVP (Windows IT Pro)]. KapilArya.com](https://images.kapilarya.com/Logo1.svg)







![[Latest Windows 10 Update] What’s new in KB5055612? [Latest Windows 10 Update] What’s new in KB5055612?](https://www.kapilarya.com/assets/Windows10-Update.png)



1 Comment
Add your comment
when I run the command “vssadmin delete shadows /for=%systemdrive% /Quiet” from the error message “Access Denied”