While working with Group Policy, many times we come to a situation when we’ve to exclude specific clients/machines from a setting. Creating a separate group for excluded clients is not perfect solution for this scenario. You can make use of Delegation tab for a Group Policy Object (GPO) to exclude clients or machines.
In this article, we’ll see how you can apply GPO to only the users or computers you want. To exclude rest of targets in your organization, you can apply the relevant process as described below. Before you delve into this method, you must ensure that elements you want to exclude should be member of your organization. For example, if you want exclude Test User account, this account should already be created.
Exclude Individual Users Or Computers From A Group Policy Object
To illustrate this process, I’ll be excluding a Test User account in this example. I’ve already created this Test User account. I’ve shown this example for a client but you can follow similar process for excluding a machine.
1. Open Group Policy Management by running gpmc.msc command.
2. In Group Policy Management window, locate the GPO object you want to exclude and in the corresponding right pane, click on Delegation. Then click on Advanced button.
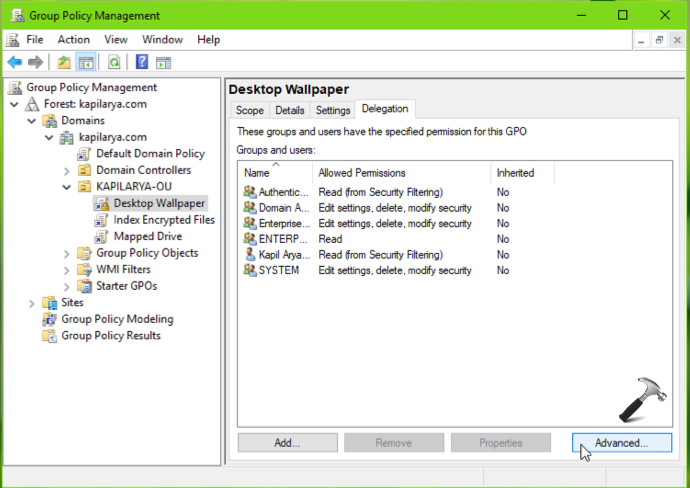
3. Next in the Security Settings window, click on Add button.
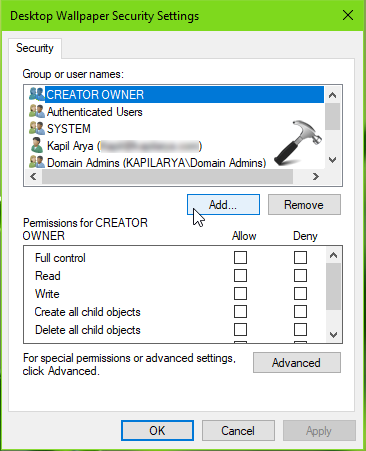
4. Then in next window, type the user you want to exclude and click Check Names. If you’re not sure about exact user name, click on Advanced and then perform search for the user and add it here. Once you listed the user, click on OK.

5. Now back in Security Settings window, select the user you’ve added in previous step. Then under Permissions, scroll down and locate Apply group policy and make a check mark for Deny. Click Apply, OK.
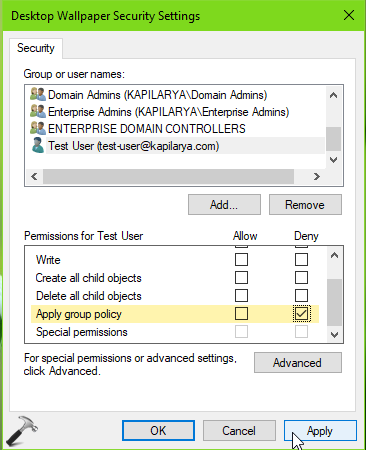
6. In the confirmation prompt appearing next, click Yes.

7. Finally, you should have that user applied custom permissions for the GPO. This means that user is now excluded from GPO.
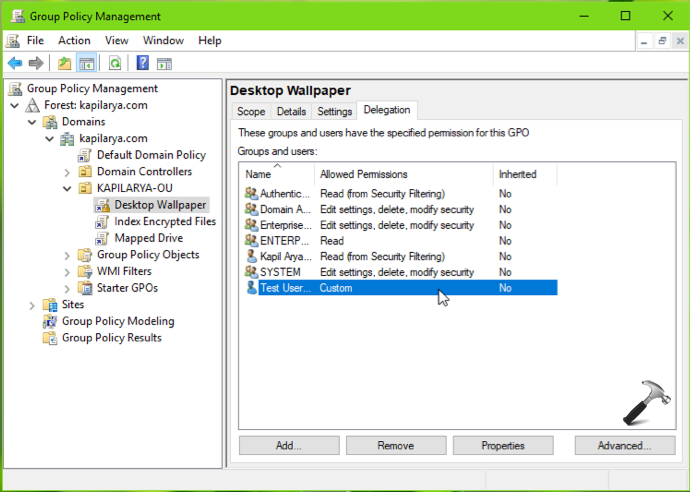
You can now close GP Management window. The settings will be applied once GP engine is updated.
That’s it!
![KapilArya.com is a Windows troubleshooting & how to tutorials blog from Kapil Arya [Microsoft MVP (Windows IT Pro)]. KapilArya.com](https://images.kapilarya.com/Logo1.svg)








![[Latest Windows 10 Update] What’s new in KB5055612? [Latest Windows 10 Update] What’s new in KB5055612?](https://www.kapilarya.com/assets/Windows10-Update.png)


6 Comments
Add your comment
Thanks for the info. Do you know how to do this in Server 2019. I couldn’t find the option in 2019 policy. Thanks
^^ These steps are already illustrated on Server 2019. Please recheck on your system.
What about the allow section….. Should read have allow checked ?
^^ It’s upto you Naveen 😎
Thank you for clear instructions. Can this be done to deny the policy for a local non-domain user on endpoint pc’s? I have local users on some operational computers whose software requires local user account with customized permissions and I dont want certain GPO’s messing with them. I have workaround in place, but your method would be ideal as I can deny at the very moment that I create the policy.
^^ Well, you can try and see if it works. I’ve not tested it that way, so can’t comment.